Introduction
I will demonstrate how to build a Hybrid DNS system between AWS and a customer on-premise environment. For this blog, I will explain how to configure the connection between the two environments. The base environments are given in the demo instructions and deployed with Cloud Formation.
Let's get started!
Set Up and Test Environment
Cloud Formation Templates
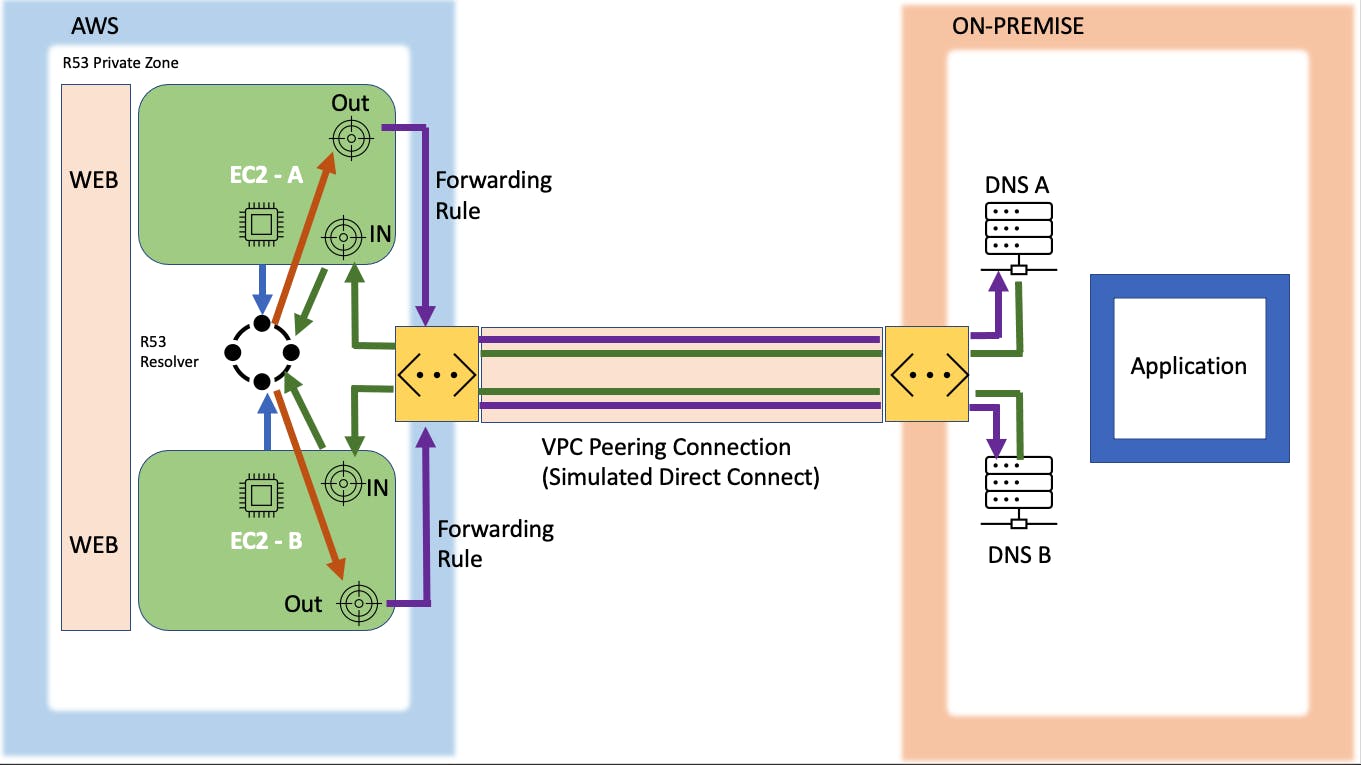
As previously mentioned, I ran the pre-configured Cloud Formation templates. The on-premises environment will be often referred to as Animals4Life or A4L. This is a random name given for the demo. After a few minutes, they reach the "create-complete" stage and I am ready to do some testing.
Ping EC2 instances to check for connectivity
I will be creating a VPC peering connection later down the line, so I want to test the connection to start.
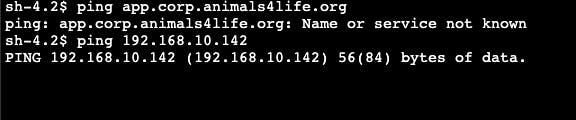
I navigated to the EC2 instance manager and connected to an AWS instance. Through the command line, I sent a ping request to the on-premise server. The response from the system is "name or service not known". This signifies that there is no connection currently. After that, I tested the connection from the on-premise server to the AWS instance. I got the same result.
With the lack of connectivity established, I will show you how I created a VPC peering connection between the two environments.
Establish Hybrid Network Connectivity
Create VPC Peering Connection
I will now create a VPC peering connection. This peering connection will be used to simulate a Direct Connect (DX). Direct Connects take a lot of time to provision and are very costly. These are long-standing connections used by corporations and not suitable for this demonstration. The VPC peering connection will function in a similar way but is much easier and cheaper to provision.
I navigate to the VPC peering connections in the AWS console and click on "Create Peering Connection".
According to the AWS Documentation, "The owner of the requester VPC sends a request to the accepted VPC to create the VPC peering connection. The accepter VPC can be owned by you, or another AWS account, and cannot have a CIDR block that overlaps with the requester VPC's CIDR block".
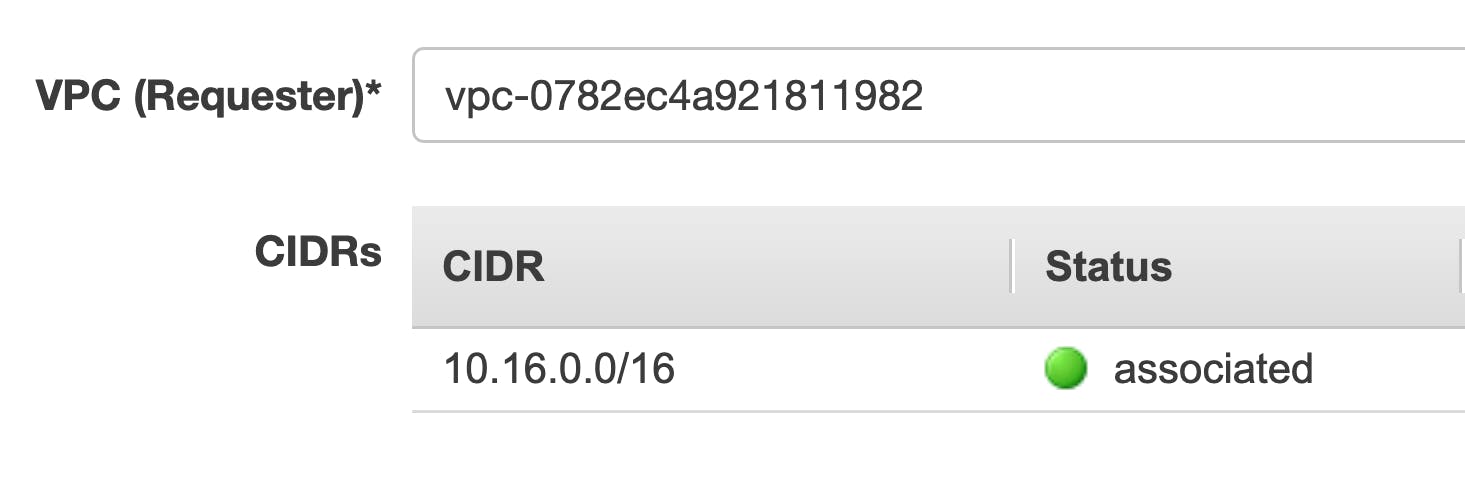
In this connection, the AWS will be the requester:
And the customer on-premise will be the accepter:
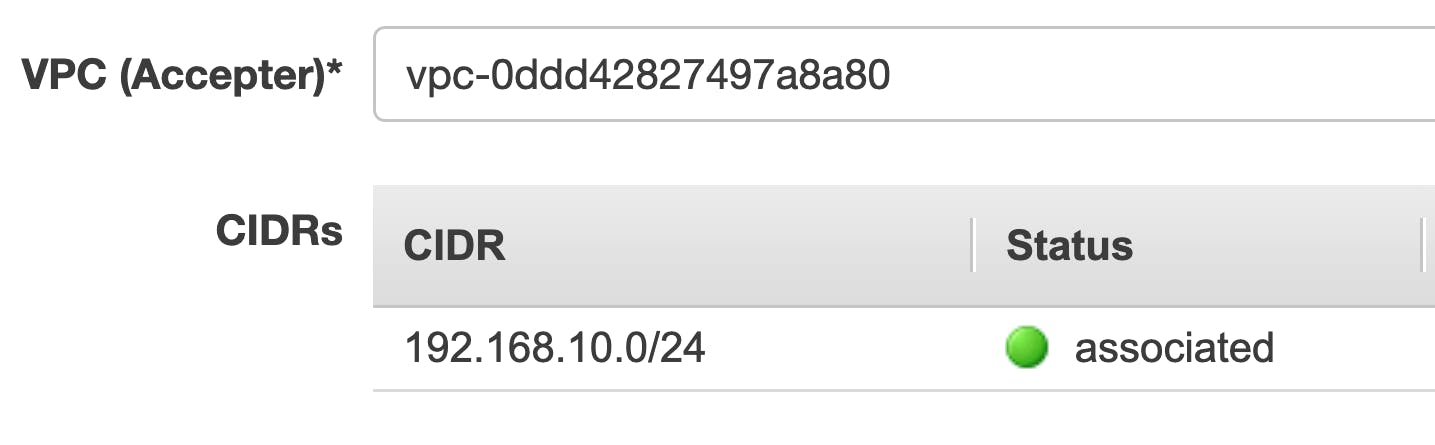
Notice that the CIDR ranges used do not overlap.
I then accepted the peering request to make the connection active.
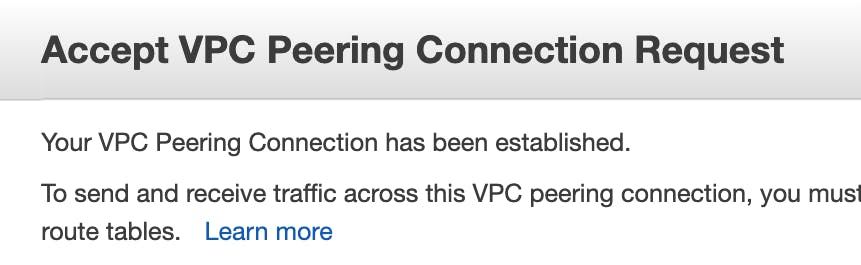
With this connection established, it's time to create the routes. They need to be configured for each direction:
- AWS -> On-Prem
- On-Prem -> AWS
Now, it's time to check the connection to make sure it is working properly. I repeat the same process that I did earlier.
- Connect to the instance via session manager
- Run a ping command from AWS to the on-premise server IP address
- Confirm the connection
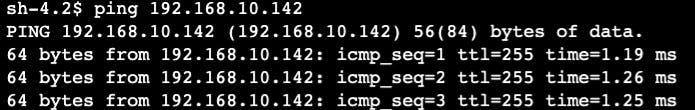
Other than the IP address, I can ping the domain name. There is no DNS integration yet as shown below. I have established only layer 3 connectivity up to this point.
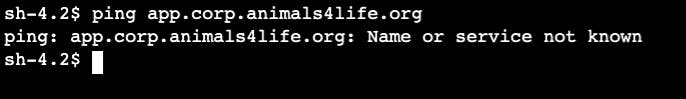
DNS Integration
In order to allow for DNS integration, I will create Route 53 endpoints.
Configure Inbound Route 53 endpoints and on-premises DNS server
These endpoints are ENI that run in the AWS environment and can be utilized by our DNS infrastructure from the customer on-premise environment.
The inbound endpoints will take in the requests and send them to the Route 53 resolver.
I navigate through the AWS console and configure the inbound endpoints as seen below:
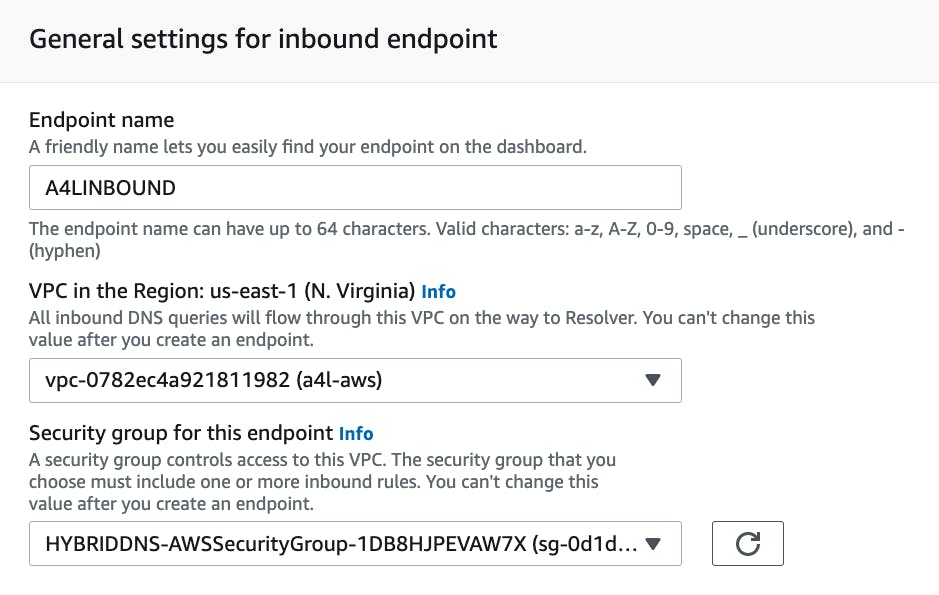
I now have the inbound endpoints in an operational state. These two IP addresses pictured below are associated with the endpoint. I will use these to establish forwarding rules.
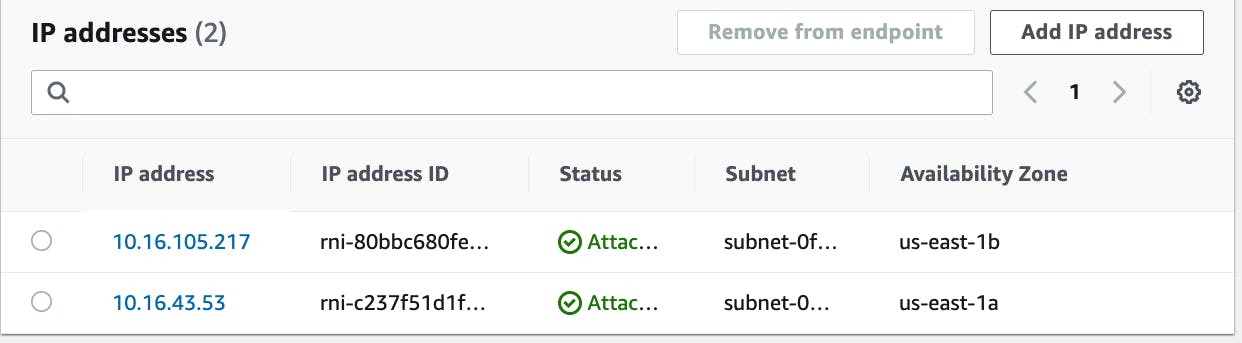
This completes all the necessary steps for the AWS side of things.
Configure the DNS servers
Whenever a query happens in the on-premises environment (aws.animals4life.org), it will forward the request to the Inbound endpoint. I use the IP addresses associated with the Inbound endpoint that I previously established. I downloaded and edited this file so I can copy-paste the information through the session manager.
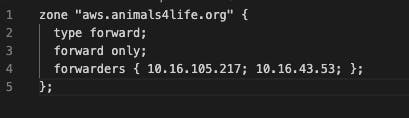
I navigated to the session manager for the DNS server. Through the command line, I used nano to edit the named.conf file and update it with the forwarding information above. The aws.animals4life.org hosted zone will now redirect to the AWS inbound endpoints.
To test that everything is working properly, I utilize the NSLookup command. In the DNS server, I go to the localhost address 127.0.0.1. This shows the forwarding information below:
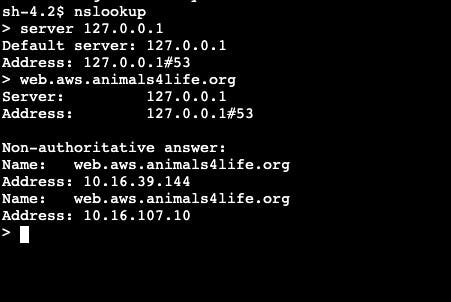
As you can see, the IP addresses in the NSLookup are the correct ones associated with the Inbound endpoints.

Navigating back to the AWS counsel to the hosted zones, you can see that there is a hosted zone with an A record for the two inbound IP addresses.
With all this configured, I just did the same process for the second DNS server in the on-premises environment.
Configure On-premise servers to use DNS servers
Through editing the script file for the ethernet configuration (eth-0), I define two IP addresses for the DNS servers.
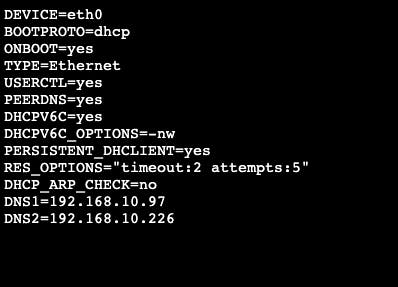
I quickly ping to check the connection to DNS.
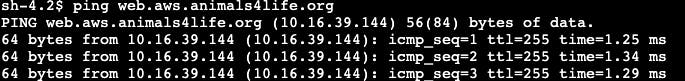
The ping request shows that we have a successful connection!
Configure the Outbound component
I once again navigate through the AWS console to create an outbound endpoint. I associated the necessary IP addresses.
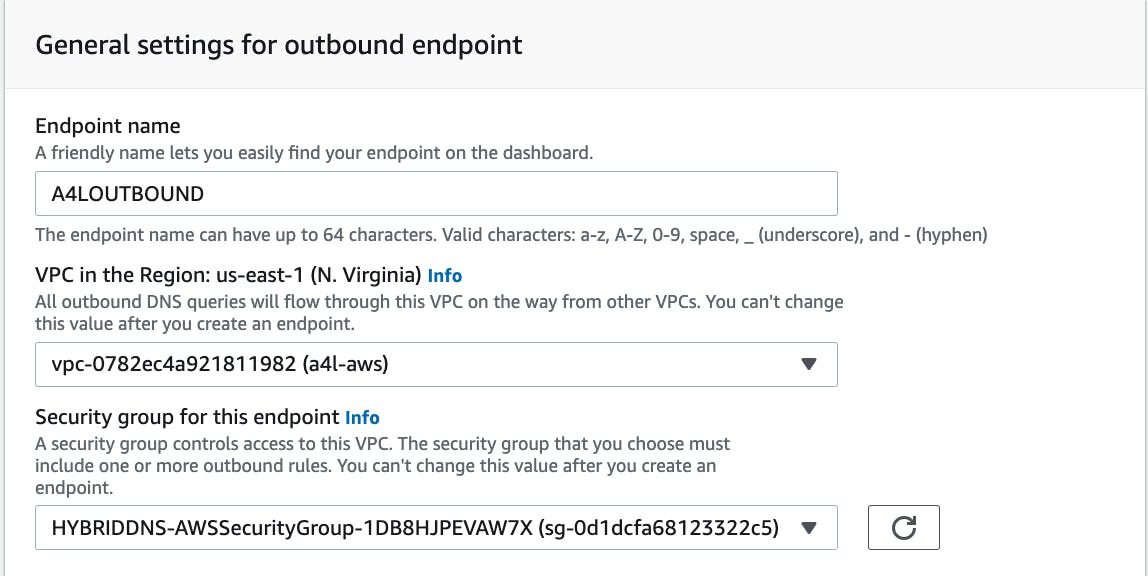
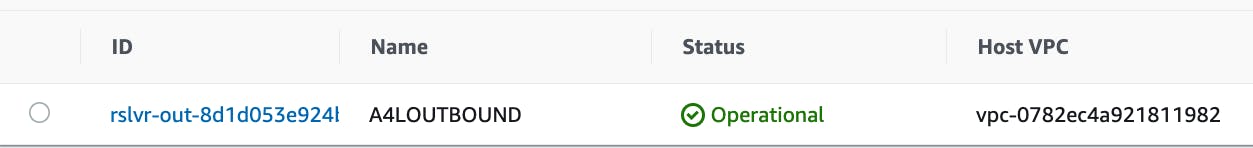
After a few minutes, the endpoint is operational.
Still in the AWS console, I configure a forwarding rule. This forwarding rule allows for the domain requests for corp.animals4life.org in our AWS VPC to our target IP addresses.
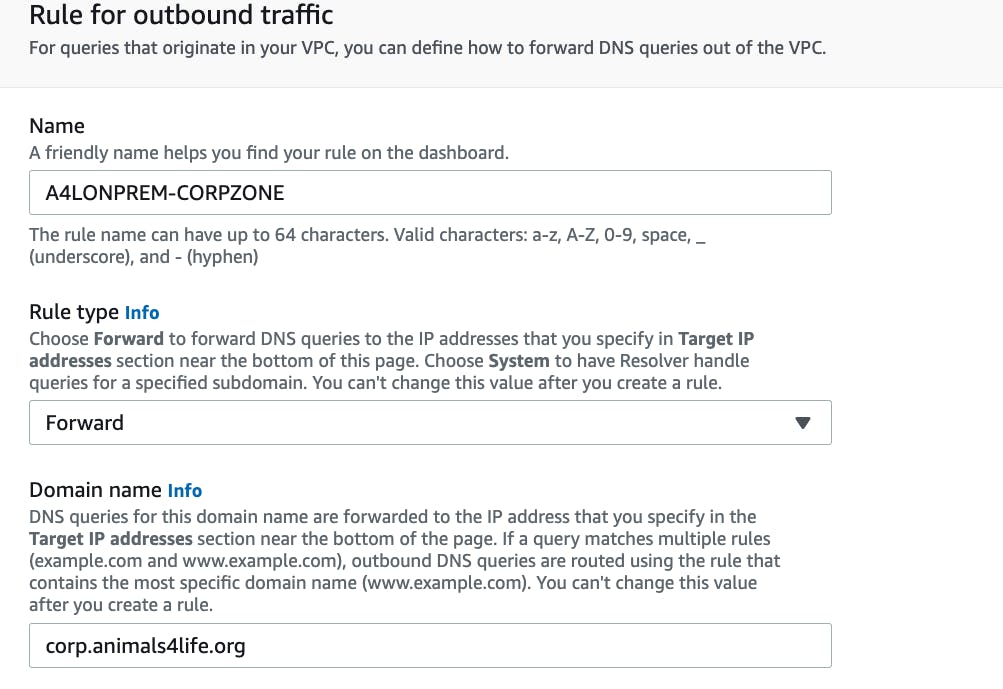
The target IP addresses that I use are the private IP addresses from the DNS servers. I grab those from each DNS server from the on-premise environment.
As I've done many times before, I test this in the session manager by sending a ping request.
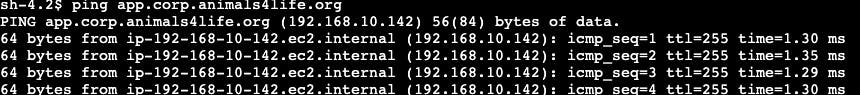
This demonstration is now complete!

Takeaways
Ping Requests
As I continue to enhance my AWS skills, many patterns are emerging. The consistent testing of connections via ping requests through the session manager is one of the most common patterns. This is a simple, quick way to make sure the configurations you implemented are working correctly.
This is not necessarily difficult, but a best practice to take going forward.
VPC Peering Connections
When testing any infrastructure, a quick and low-cost way to create a connection is through VPC peering. Take the few steps of adding the opposite sides of the connection and accepting the connection. You are up and running quickly and can test more elaborate infrastructure. This is a great tool when you are learning all these services.
Session Manager
Getting comfortable with the session manager and the command line is a skill I will take forward with me. The command line will always be a sticking point for many people. I highly recommend getting more practice with navigating through an instance and updating files using it. Additionally, learn how to use command line text editors such as Vim or Nano. You will be mostly changing 2-3 lines at once and not writing whole files. Using a command-line text editor can save a lot of time in the long run.
Thanks for reading!
I appreciate everyone who made it this far! I am looking for Junior opportunities working with AWS.
If you would like to contact me:
- Check out the resume I built on AWS: Cloud Resume
- Connect with me on LinkedIn or follow me on Twitter
- Thanks to Adrian Cantrill for the great demo, check out his courses: https://learn.cantrill.io/